Squeaky Clean: Security Hygiene with DataBee
Enterprises have an ever-growing asset and user population. As organizations become more complex thanks to innovation in technology, it becomes increasingly difficult to track all assets in the environment. It's difficult to secure a user or device you may not be aware of. DataBee can augment and complement your configuration management database (CMDB) by enhancing the accuracy, relevance, and usability of your asset, device, and user inventory, unlocking 3 primary use cases for security teams:
-
Security Hygiene
-
Owner & Asset Discovery
-
Insider Threat Hunting
Security Hygiene
DataBee for Security Hygiene can help deliver more accurate insights into the assets in your environment while automatically keeping your asset inventory up-to-date and contextualized. Bringing more clarity about your users and devices in your environment, enables your business to enhance its security coverage, reduces manual processes, increases alerts’ accuracy, and more rapidly responds to incidents.
Security hygiene uses entity resolution, a patent pending technology from Comcast, to create a unique identifier from a single data source or across multiple data sources that refer to the same real-world entity, such as a user or device. This technique is performed by DataBee helps reduce the manual entity correlation efforts by analysts, and the unique identifiers can be used to discover assets and suggest missing owners.
DataBee supports ingestion from multiple data sources to help keep your security hygiene in check, including a variety of traditional sources for asset management such as your CMDB, directory services, and vulnerability scanner. It also can learn about your users and devices from non-traditional data sources such as network traffic, authentication logs, and other data streamed through DataBee that contains a reference to a user or device.
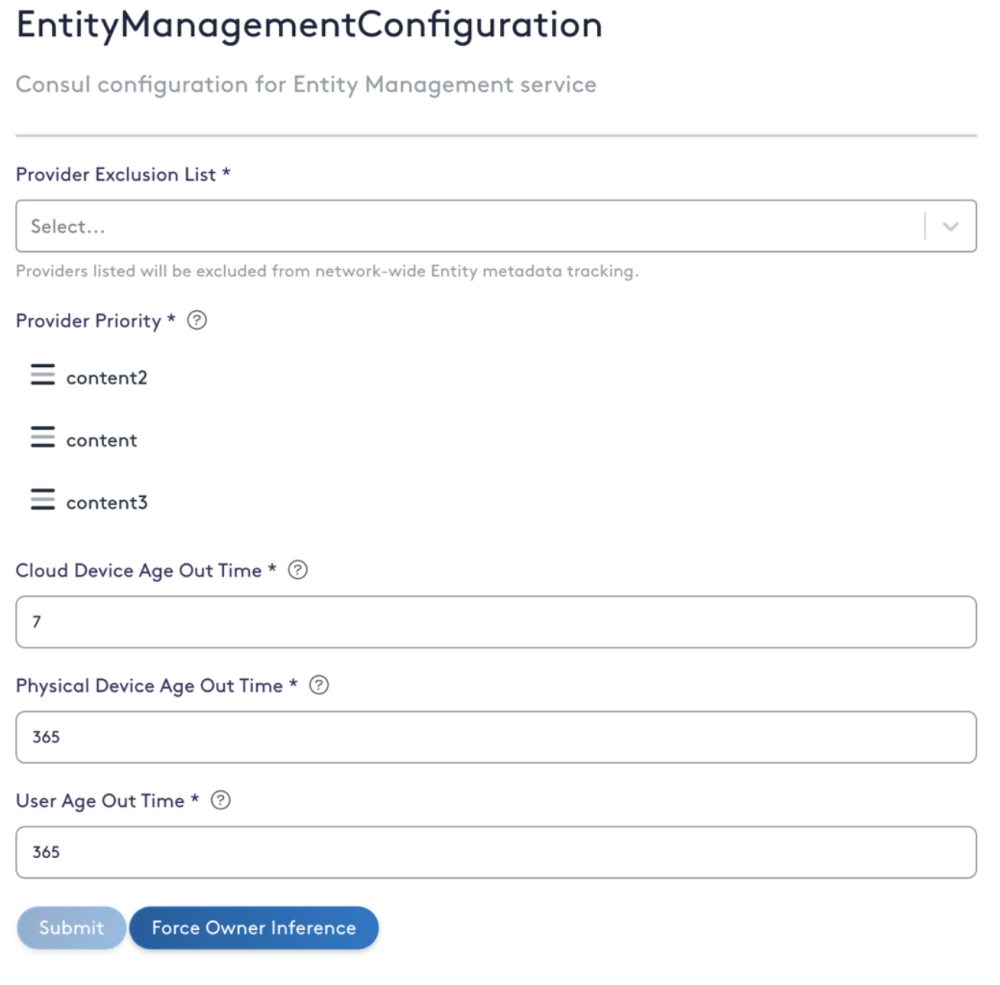
DataBee can also be used to exclude data sources and feeds from entity resolution that provide little fidelity for entity-related context and support feed source prioritizations. These inputs are used when there is collision or conflicting information. For example, if a device is first seen in network traffic, preliminary information about the device will be added to DataBee such as the hostname and IP. Another example is when your CMDB updates a device’s IP. DataBee will use this update to overwrite the associated IP if the CMDB feed is prioritized over the network traffic information.
Owner and Asset Discovery
Organizations often struggle to assign responsibility for resolving security issues on assets or devices, many times due to unclear ownership caused by gaps in the asset management process, such as Shadow IT and orphaned devices. DataBee can provide a starting point to identifying and validating the owner of a device. When a new device is discovered or the owner is not indicated in CMDB, DataBee will leverage the events streaming through the platform to make a suggestion of the potential owners of the asset. The system tracks who logs into the device for seven days after discovery and uses statistical analysis to suggest up to the three most likely owners.
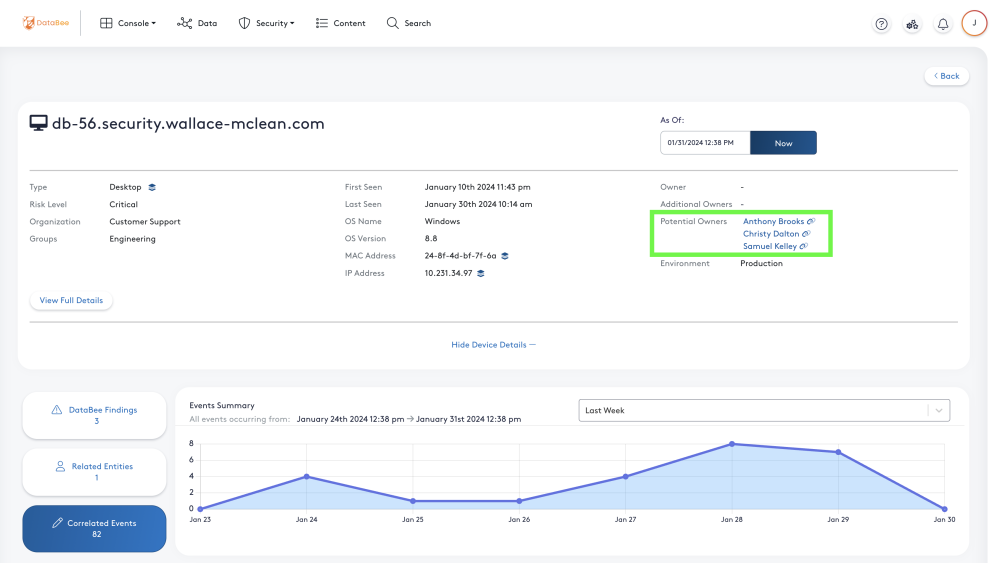
The Potential Owners are listed in the Entity Details section of the Entity View page that can be expanded to quickly validate the ownership. Once security analysts are able to validate the owner, the system of record can be updated and DataBee will receive the update.
As organizations become more complex thanks to innovation in technology, it can become increasingly difficult to track all assets in the environment. DataBee provides User and Device tables to supplement existing tools. Orphaned assets remain unknown and often unpatched, creating unmonitored levels of increasing risk. Shadow IT is a growing problem as more cloud-based solutions become easily accessible. Entity resolution maintains an inventory of known assets in your organization. This enables continuous discovery of assets that would otherwise slip through the cracks based on events streamed through DataBee.
Insider Threat Hunting
Insider threats are people, such as employees or contractors, with authorized access to or knowledge of an organization’s resources, that can cause potential harm arising from purposeful or accidental misuse of authorized user access. This can have negative effects on the integrity, confidentiality, and availability of the organization, its data, personnel, or facilities. Insider threats are often able to hide in plain sight for many reasons. There is complexity in cross-correlating logs of an individual's activities across various tools and products. Further, the data is siloed, making it difficult for security analysts to see the full picture. DataBee’s security, risk, and compliance data fabric platform weaves together events as they stream through the business context needed to identify insider threats.
DataBee leverages entity resolution to create an authoritative and unique entity ID using data from across your environment that is mapped to real people and devices to enable hunting for insider threats in your organization. Entity resolution aggregates information from multiple data sources, merges duplicate entries, and suggests potential owners for devices and assets. By correlating and enriching the data before storing it in your data lake, DataBee creates an entity timeline, associating each event with the correct entity at the time of its activity.
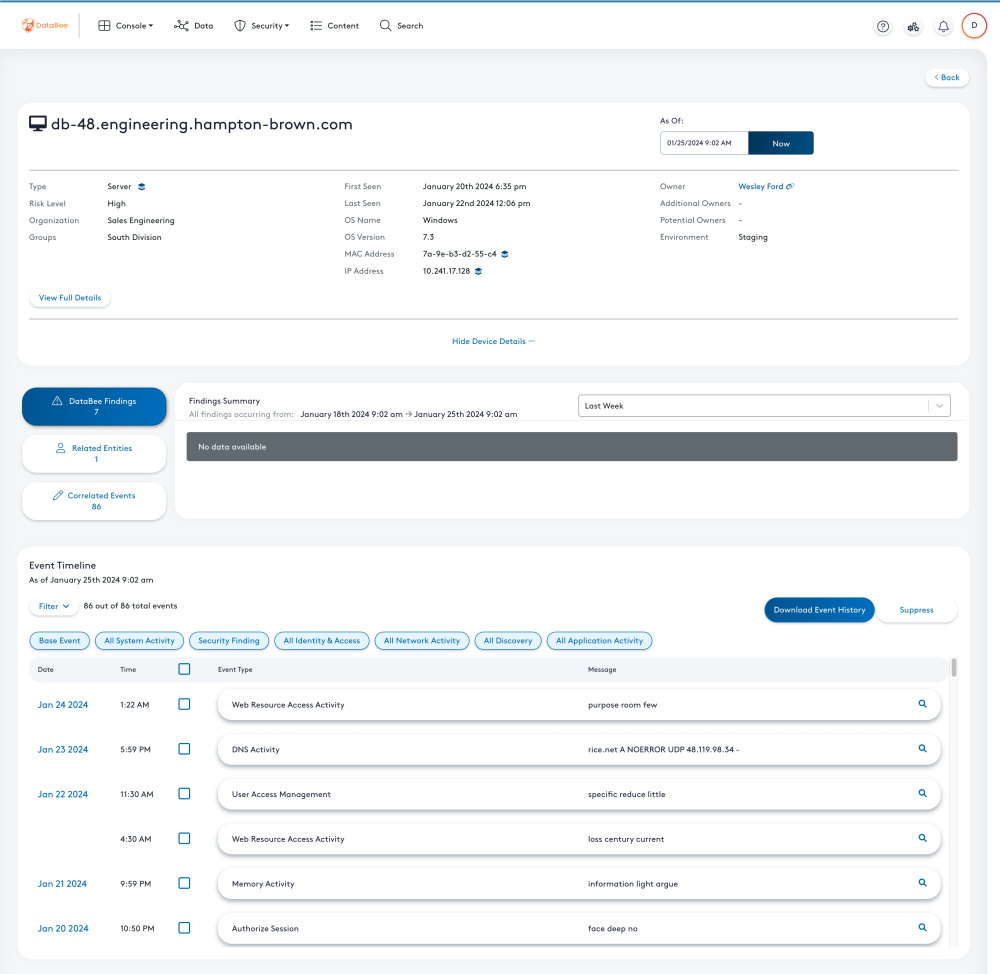
These views enable insider threat hunting by allowing security analysts to see the activities conducted by a user and the related business context in a single view to identify potential malicious behavior. The interactive user experience is intended to make leveraging the Open CyberSecurity Framework (OCSF) formatted logs more accessible to all security professionals. Within the Event Timeline, security analysts can filter the events based on type to focus investigations. Clicking on the event will show the mission critical fields needed to decide if the event is interesting. Clicking on the magnifying glass icon allows you to inspect the full event. DataBee enables one-click pivoting to related entities to simplify diving deeper into the investigation. The views are powered by the data in the data lake. Therefore, the data is available in OCSF format for threat hunters to continue their investigations in traditional tools like Jupyter notebooks to meet hunters where they are with their data.
Take a look under the hood of DataBee v2.0 and DataBee for Security Hygiene
Are you ready for an enterprise-ready security, risk, and compliance data fabric? Request a custom demo to see how DataBee uses a unique identifier that can be used to augments your CMDB and help deliver more accurate insights into the assets in your environment.