Expert Insights: GRC and the Role of Data
Since I joined Comcast Technology Solutions (CTS) and the DataBee™ team back in late March, I’ve been awed and challenged by how many different roles the DataBee data fabric platform is relevant to. Is it for security analysts? Threat hunters? Data scientists? GRC professionals? Yes, yes, yes and yes… essentially, DataBee is relevant to anyone in an organization who needs data to understand, protect and evolve the business.
Let’s get to know some of the amazing people who rely on data every day to do their jobs and help their organization be successful!
Governance, Risk & Compliance (GRC)
The function of GRC is critical – when it is correctly implemented, it is a business enabler and revenue-enhancer; when it is poorly managed or even non-existent, it can be a business inhibitor, leaving an organization vulnerable to compliance violations and increased cyberthreats.
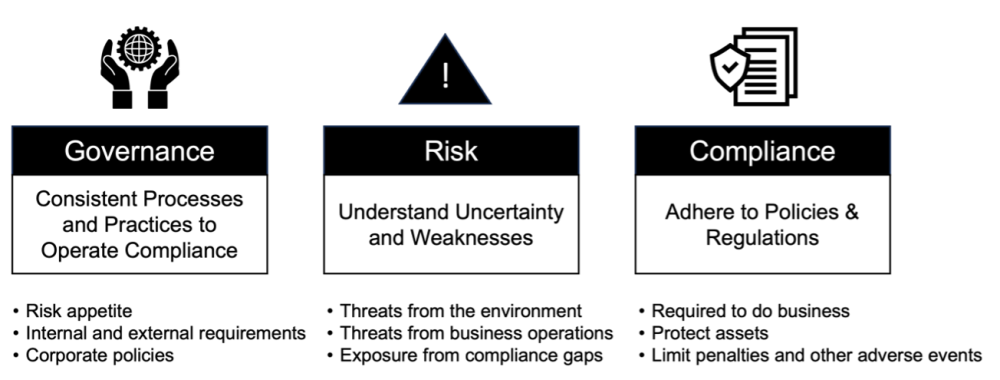
GRC programs are set of policies and technologies that align IT, privacy, and cybersecurity strategies to their business objectives.
I recently had the good fortune of meeting Rob Rose, a Manager on the Cybersecurity and Privacy Compliance team here at Comcast, and I enjoyed my conversation with him so much that I immediately hit him up to be one of our spotlight experts.
Working to achieve a more secure privacy and cybersecurity risk posture
[LC] Rob, tell us about what you do as Manager, Cybersecurity and Privacy Compliance here at Comcast.
[RR] At the highest level, my role at Comcast is to help the company achieve a more secure privacy and cybersecurity risk posture. This takes shape as leading an initiative called ‘Controls Compliance Framework’ (CCF) which is broken down into two sister programs: ‘Security Controls Framework’ (SCF) and ‘Privacy Controls Framework’ (PCF). The team I lead creates a continuous controls monitoring (CCM) product that business units across Comcast can use to monitor their adherence to privacy and cybersecurity-related controls.
Creating, and maintaining, this product includes collaboration with multiple different teams in the company, starting with the process owners of each control activity that helps to mitigate risk (e.g., the Corporate User Access Review team):
- Collaboration with process owners: My team first works with the process owners to understand how the process is designed and should operate, and what actions the various Business Units across Comcast are expected to complete.
- Document requirements: We then learn from process owners how and where they store the data to support their control (e.g., Oracle Databases, ServiceNow, etc.) and from there we document requirements to bring to our development team.
- Report on privacy and security posture: Once our development team has ingested all the disparate data from multiple process owners and developed our product based on the requirements we documented, we bring this product to Business Units, with the goal of providing them a single pane of glass view into their overall privacy and security posture.
GRC Challenges
[LC] What would you say are the 3 biggest challenges faced by GRC and compliance experts?
[RR] There are a few keys challenges that we run into as a GRC function, and fortunately, compliance data leveraged in the CCF program can address them.
- Clean Data – the first issue is the cleanliness and usability of the data. As a GRC function, we rely on process owners throughout the company to provide us with data. Frequently, however, we see issues with both data cleanliness and ownership in the data that is provided to us. When we bring this data to Business Units, who work day in and day out with the assets they own, they often provide the feedback that there is something amiss in the data. This can be turned into a positive as we can bring this feedback back to the process owners, who can then clean up the data on their end, making the data quality better for the entire company.
- Awareness – Often times when we alert Business Units of compliance actions that need their attention, we discover that they were unaware of these requirements. This awareness creates some ‘knowledge transfers’ that we must do to inform Business Units of the need for the actions, and the importance of the actions. This helps to increase the overall cybersecurity and privacy awareness of the Company.
- Prioritization – Akin to point B, since Business Units are often not aware of the privacy and security related actions they need to take, they have not planned the resource capacity into their roadmap to complete those activities. Helping to prioritize which actions are ‘must do’ right now, as opposed to which actions can wait, has been something we’ve been working on with our program. To help with this, we’ve been driving towards risk-based compliance, noting that while all systems and assets need to meet cybersecurity requirements, certain systems and assets are a higher priority to meet these requirements based on the types of data that the system utilizes.
The rewards of the job
[LC] What are some of the most rewarding aspects of your job?
[RR] We’ve had some real success stories over the past few quarters where Business Units have gone from a non-compliant state to a highly compliant state. This has come from a combination of presenting Business Units with insights through data so they are aware of where they have gaps, and from helping them understand what actions they need to take. Seeing a Business Unit make this transition from non-compliant to compliant is incredibly rewarding, as we know that we’ve helped make the company more secure.
Collaboration
[LC] What other teams or roles do you interact with the most as you go about your job day-to-day?
[RR] As a GRC professional, we’re in a unique position where we interact with individuals at all levels of the business. This includes the first line of defense (Business Units), the second line of defense (process owners, Legal, other teams within Comcast Cybersecurity), and the third line of defense (Comcast Global Audit). We have the benefit of working with both very technical teams of developers and system architects, as well as with very process driven teams who define what requirements the company should be meeting. In addition, in our position, our team works with top level executives from a reporting standpoint, as well as the front line workers who are actually implementing changes to systems and applications to make the company more secure!
The role of data in GRC
[LC] How do you use data in your job, and what type of data do you rely on?
[RR] As a GRC professional, the ability to have clean data provided to us is the keystone to our success. The Controls Compliance Framework product my team and I work on is dependent on data coming in from disparate data sources so we can cleanse and aggregate it to provide meaningful insights to Business Units.
At the highest level, you can break down the types of data that we need into a few different categories:
- Application data: What applications exist in the environment, who owns those applications, and what level of risk does the application present -- e.g., does the application use customer data, proprietary Comcast data, etc? Does the application go through User Access Reviews on a set frequency, and has it been assessed to confirm it was developed in a secure way?
- Infrastructure: What underlying assets or infrastructure support those applications? What servers are used to run the application? Are they in the cloud or on-prem? What operating system is the server running? Is the server hardened, scanned for vulnerabilities, and does the server have the necessary endpoint agents on it (e.g., EDR)?
- Vendor information: What vendors do we engage with as an aspect of our business, what data do we share with the vendor, and what assessments have been completed to confirm the vendor will handle that data securely?
For each of these types of data, we also need data to support the completion of the processes around that data. Have all assessments been done on the application, asset, vendor, and do they meet all the required controls?
As you can imagine, these data sources are all in different locations. One of the key aspects of the program we run is to pull all of this data into one location and provide it in a single pane of glass view for business units so they can have one easy location to go to to understand their risk posture.
The GRC questions that data helps answer
[LC] Can you give us an example of the kinds of questions you’re looking to answer [or problems you’re looking to solve] with data?
[RR] The biggest question I’m looking to answer as a risk professional is what the overall risk posture of the company is. Do we have a lot of unmitigated risk that could expose us to issues, or are we generally covered? This question is most easily answered with the data that was described above (the role of data in GRC).
GRC vs. Compliance
[LC] How would you describe the difference between GRC and compliance? Or are they one-and-the-same?
[RR] The ‘C’ in ‘GRC’ stands for Compliance. Compliance is a huge piece of what I do as a GRC professional. Making sure that the company is complying with the necessary standards and policies (compliance) and lessening the exposure we have as a company and the impact of that exposure (risk) is pretty much what my entire day is filled with! We then present these insights to executives so they can be aware and take action to adhere to standards and policies as needed (governance).
A random data point about our GRC expert
[LC] Rob, if you could go back in time and meet any historical figure, who would it be and why?
[RR] Wow this is a tough one that I think could change day by day. I recently took a trip to Rome and we visited the Sistine Chapel while we were there. I was in such awe of the work that Michelangelo did. I think I’d like to meet someone like Michelangelo as the arts are an area that is so foreign to me and how I think. I’d love to pick his brain to find out if he knew what he was creating would be a work that was revered and visited by millions of people for centuries to come, to understand his artistic thought process, and to learn more about his life.
Parting words of wisdom
[LC] Any other words of wisdom to share?
[RR] To my other GRC colleagues out there, I am sure you run into the same struggles of trying to get Business Units to comply with internal company policies and standards. The implementation of data-driven tools have made it significantly easier to assist BUs in becoming compliant. The feedback that we’ve gotten is that utilizing data, and putting it in a simple and straightforward tool, has helped to ‘make compliance easy’. Let’s all keep striving to find ways to make it as easy on the people whose main job is not compliance to fit compliance into their work!
DataBee for GRC
As Rob mentions, the Comcast GRC team is charged with pulling all kinds of data – application, infrastructure and vendor data -- into one location, essentially providing a “single pane of glass view” to Business Units, making it easy for these Business Units to see and understand their risk posture. The GRC team uses the internally developed data fabric platform that DataBee is based on to do this, and its use has helped to drive those improved compliance rates that Rob mentioned, as well as other improvements in Comcast’s overall compliance and security posture. (An aside – I think that’s pretty cool.)
DataBee v1.5 was recently launched, and with it a continuous controls monitoring (CCM) capability that provides deep insights into the performance of controls across the organization, identifying control gaps and offering actionable remediation guidance. Check out the CCM Solution Brief to learn more.
Thanks to Rob for a great interview!