Take the drama out of compliance audits and scale your GRC program with data
DataBee® CCM delivers consistent and accurate compliance dashboards and reports that measure risks and control effectiveness.
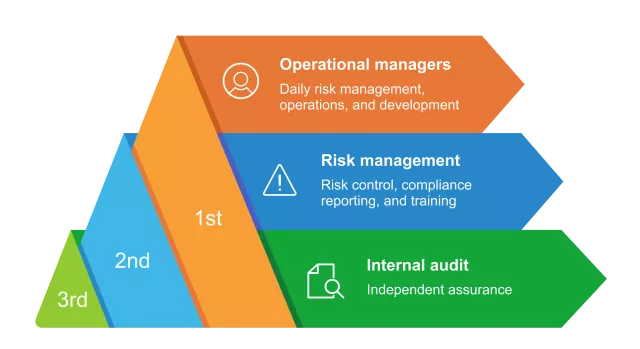
Designed to put data at the center, governance, risk, and compliance (GRC) leaders and analysts save time on audit preparedness and achieve fast compliance answers and resolutions. By weaving and enriching multiple data sources into security data fabric, DataBee enables all three lines of defense to report on the same contextualized insights on data they trust.
Leave spreadsheets and point-in-time compliance reporting relics of the past. DataBee makes continuous controls monitoring a reality.
Achieve continuous controls monitoring with DataBee
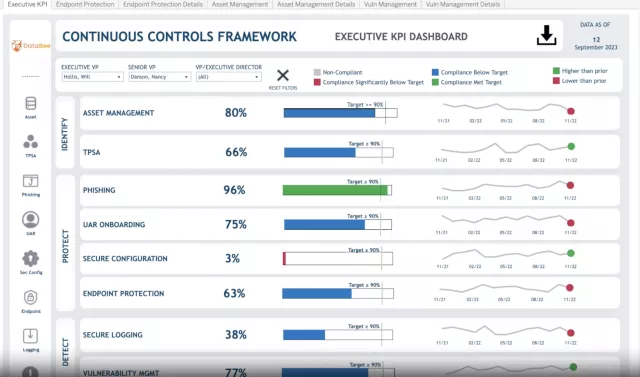
Quickly and proactively deliver measurable and accurate CCM metrics about your security posture and cyber-risk management investments.
Robust and actionable compliance reporting
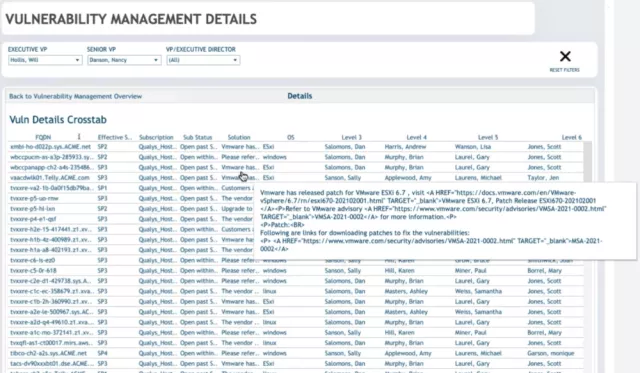
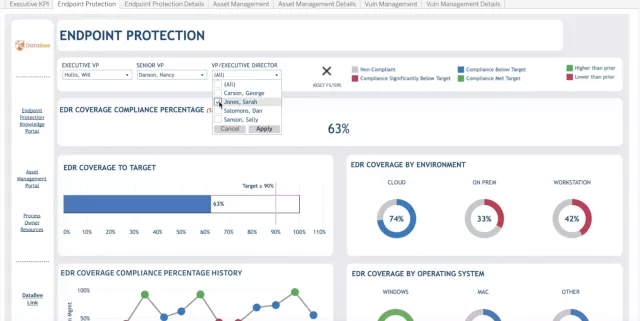
DataBee automatically identifies and connects data required to assess compliance and controls. GRC teams can shift away from point-in-time compliance reporting to continuously refreshed dashboard views. DataBee ensures data quality and makes it easy to monitor compliance trends and shape reports in Tableau and Power BI using your data and business policies and standards. With more actionable compliance insights, you can be more confident about your security posture and focus on closing gaps.
Enhanced compliance lifecycle communication
DataBee defines compliance gaps against your control targets to prioritize critical remediations and address at-risk resources. Reports are based on management structure, enabling process owners and business managers to collaborate on compliance data and guidance. This reduces confusion about who in the organization is responsible and who is accountable. GRC teams can make more informed recommendations about business strategy and future security investments using enriched data from your organization.
Continuous controls monitoring is a game changer for security transformation and outcomes to ensure that security controls are optimally performing and organizations are compliant. CCM allows for proactive security and risk management to keep organizations on track with changing regulations and requirements. And as a result, a strong, data-centric CCM program and consulting from GRC experts like that from DataBee can boosts cross-department communication and accountability while strengthening your security posture.